Trust us!
Trust us!
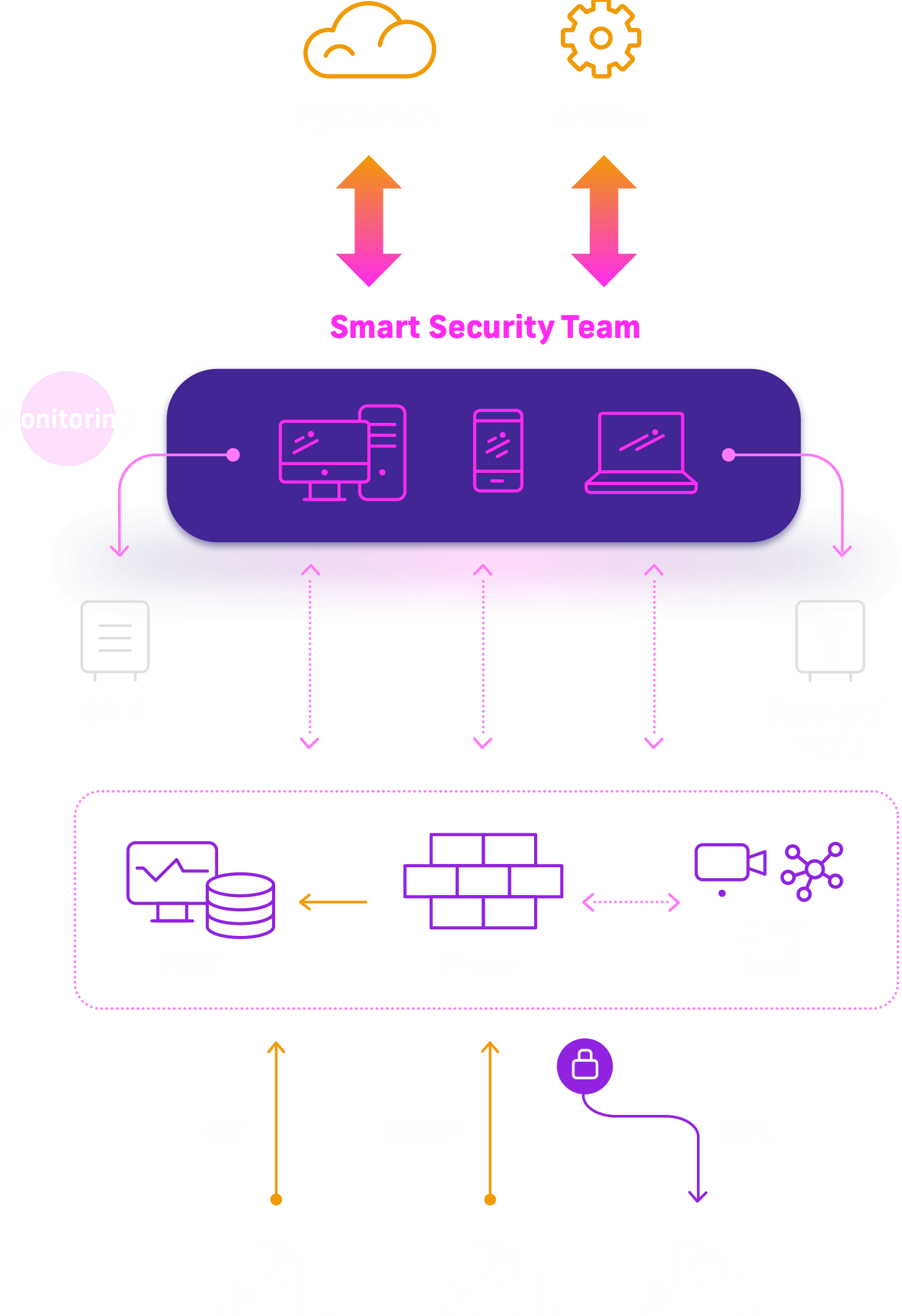
While we take care of the daily activities, you will be able to spend this time on business development, conceptual tasks and strategic environmental activities. Together with our engineers, you will make critical updates and works that affect the business continuity.
Smart security includes, among others:
Smart security includes, among others:
- Change management
- Security management
- Monitoring of environmental health and the quality of its components
- „Best Practices” audit of the environment
- Modifications and updates of environmental elements as part of audit recommendations
- Detection of vulnerability of elements forming the environment
- Reporting when incidents are detected
- Consulting on existing solutions
- Dedicated engineer as a single point of contact (TAM)
- Reporting of works according to the established SLA
- Risk Monitoring and Response Automation (SOAR)
Smart Security
is for you if:
Your organization suffer from the lack of adequate staff
to ensure security and maintenance of IT services at the appropriate level
Your IT resources are insufficient
to take care of the daily, often tedious administrative duties.
Your level of security is not good enough
or you don't know how to verify it.
How do
we do it?
1/3
Service
implementation
What do you gain from
Smart Security?
- Round-the-clock monitoring of elements covered by the service
- Immediate detection of problems and failures
- Ongoing analysis of trends that may lead to failures or downtime
- Bidirectional confidentiality and integrity of communication
- Protection of sensitive information, through segmentation of environment into security zones
- Secure methods of managing the operator access (accounts/passwords/password vault)
- Full accountability of actions recommended by the client's personnel and performed by Smart Security operators
- Several parallel channels for registering customer requests (portal, email, telephone)
- Current view of the status of executed orders
Smart security
technologies










Advanced technology
in your company
Advanced technology
in your company
IT security management services include your network, endpoints, vulnerability management, monitoring and analysis. We expand your security activities to connect people, processes and technologies to provide 24/7 support.
Security infrastructure management
Firewall management
Management of protection MAIL/WEB
WAF/DAM management
NAC Administration
SSLVPN administration
Security strategy
Network infrastructure management
Router management
Switch management
Wifi management
Server virtualization
Load balancer administration
Architecture planning and development
Management of systems
Maintenance of operating systems
Management of SIEM systems
Cloud services
Other
SOC service
Log management
Compliance reporting
Monitoring of security events
Support service
Helpdesk
Troubleshooting
Service
Subscription plans
The fee for using the smart security service is based on a subscription of hours to use each month.
BASIC
A package of work orders to be used in ON-DEMAND mode
Change management in existing IT security systems
Monitoring and ongoing administration of systems
Basic reporting
STANDARD
+ INCLUDES BASIC
“Best practices” audit of customer's systems
Modifications and system updates as part of audit guidelines and recommendations
Vulnerability detection using professional tools
Consulting in the scope of existing security solutions
PREMIUM
+ INCLUDES BASIC I STANDARD
Dedicated engineer as single point of contact (TAM)
Reporting of work orders in accordance with the established SLA
Threat monitoring and response automation (SOAR)
Opinion
Customers
Try out
Smart Security!
If you want to know more or need help in choosing the right plan!